Password strength validation with ZXCVBN
As I was going thought a cryptography course learning about modern brute-force and password entropy (brute-force complexity) estimation techniques, I’ve came with idea, that it would be great if user password strength requirements would be based on the estimated entropy rather then a set of primitive rules like “a least 8 characters one capital, digit and a special symbol” that at the end leads to passwords hard to remember and still easy to crack.
Not a surprise — I wasn’t wasn’t first. A surprise — how great job in that area is already done and how long time ago.
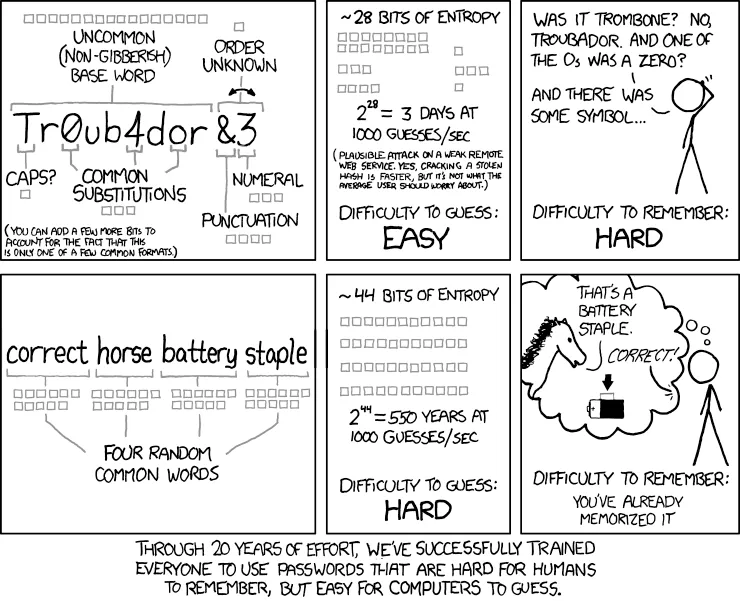
Someone even came up with a great comic, registered as xkcd.com/936/, that explains the issues way better then me. ↓
ZXCVBN
The guys from Dropbox addressed the problem back in 2012, coming up with JS library (dropbox/zxcvbn) that nowadays is ported to many other platforms as well.
The JS library available on npm and weights less the 400K (compressed) estimates entropy considering 30’000 most common password, 30’000 most common english word (according to wiki), almost 15’000 most popular names and surnames (according to US census), almost 20’000 most popular words from TV and movie names, most common L33T substitutions, date patterns, repeats, sequences, keyboard layouts (qwerty and dvorak), common an mac numpad layouts, and not least important optional array of password owner related words.
The results are amazing, try it yourself.
The usage is super simple as well. Example ↓
import zxcvbn from 'zxcvbn'
const result = zxcvbn('Tr0ub4dor&3')
console.log(result)output
{
password: 'Tr0ub4dor&3',
score: 4,
guesses: 100000000001,
guesses_log10: 11.000000000004341,
feedback: { warning: '', suggestions: [] },
sequence: [
{
pattern: 'bruteforce',
token: 'Tr0ub4dor&3',
i: 0,
j: 10,
guesses: 100000000000,
guesses_log10: 11
}
],
calc_time: 4,
crack_times_seconds: {
online_throttling_100_per_hour: 3600000000036,
online_no_throttling_10_per_second: 10000000000.1,
offline_slow_hashing_1e4_per_second: 10000000.0001,
offline_fast_hashing_1e10_per_second: 10.0000000001
},
crack_times_display: {
online_throttling_100_per_hour: 'centuries',
online_no_throttling_10_per_second: 'centuries',
offline_slow_hashing_1e4_per_second: '4 months',
offline_fast_hashing_1e10_per_second: '10 seconds'
}
}Thoughts
I’ve spent several hours to find a worthwhile alternative — no results (zxcvbn ports to other platforms were not considered).
That really surprising that the technology got so narrow adaptation since 2012,
even the most widespread services (Google, Microsoft, Facebook) allowed me to register using Pa$$w0rd2.
As well as I haven’t neither zxcvbn neither any worthy alternative in Auth0 and Microsoft B2C provided solutions.
On the good side, the npm trends shows the adaptation started growing really fast within last two years.
IMHO when there is an option to delegate credential management to a third party, via OpenID Connect or Federated Authentication for example, I’d always choose that, but if I’ll ever need to implement credential management myself — the ZXCVBN will be a part of a solution.
P.S.
The other thing that I’ve learned thanks to the course and ZXCVBN is that, the few password I have that are not auto-generated — really suck. The good thing, there is a correcthorsebatterystaple.com to generate high entropy password to remember :)
